Comprehensive insider threat management software to ensure compliance
VigilancePro user activity monitoring & audit software is used by Police and other security agencies to meet their Lawful Business Monitoring (LBM) requirements, overseeing adherence by their officers and staff to Professional Standards Guidelines. In the sector this is sometimes also referred to as Protective Monitoring or Insider Threat Management & Audit Systems (ITMAS).
VigilancePro continually monitors the activities of officers and staff while they’re using corporate systems, applications and devices. It provides a holistic view of activity so that breaches of policies and possible transgression from prescribed standards of behaviour can be quickly identified and investigated, and appropriate action taken.
Lawful Business Monitoring (LBM) at a glance
Monitor all user activity in real-time regardless of device, system or application
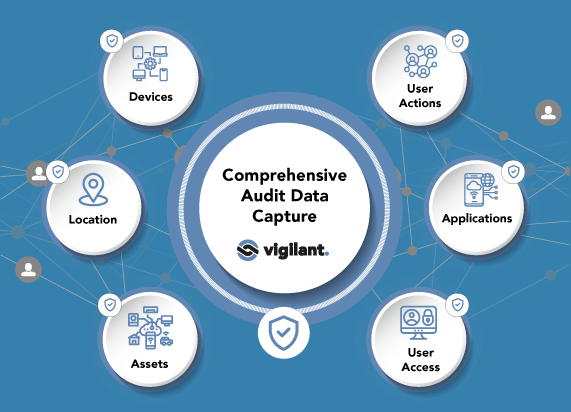
Capture a complete user-centric audit trail of officer and staff actions
Enable context-based policies or responses to be automatically applied
Apply trigger-based logging so that specific actions or events can instigate or increase activity audit for a specific user
Easily cross-reference LBM audit data with information from other applications to enable more proactive monitoring measures and tighter governance
Easy to use insider threat monitoring & audit software
VigilancePro is designed to be straightforward to use by Professional Standards analysts, investigators & digital exploitation personnel. By collecting activity audit data at the point of user action, Professional Standards teams no longer need to manually extract, amalgamate and interpret audit logs from disparate applications; or rely on IT department resources for access to system data. VigilancePro’s comprehensive reporting and search capabilities speed up the identification and investigation of officer and staff activities that breach prescribed standards.
Download Datasheet
VigilancePro in Operation
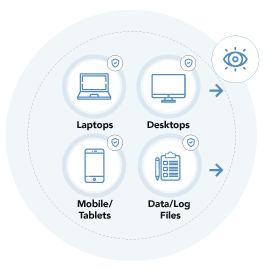
VigilancePro sees all that the user sees and all that the user does
VigilancePro monitors all user activity on endpoint devices. In simple terms, VigilancePro ‘sees what the user sees and what the user does’ at the point of interaction and in real time.
Monitoring, recording and analysis is persistent, regardless of connection status; allowing for retrospective visibility and auditing if a device is temporarily offline.
VigilancePro enables proactive identification and investigation of breaches of policy
- Information on activities, content and location is gathered from all devices and applications across the organisation, and combined into a single user-centric view to provide a complete understanding of the context of actions
- Flexible dashboards allow activities of potential concern to be automatically highlighted; and for all events to be searched, queried or reported upon for ease of investigation
- User activity monitoring and audit data recording levels can be applied, changed, and higher levels initiated at any time for individuals under active investigation
- Integration with data from other Force applications and system audit logs is supported, enabling sophisticated cross-referencing of information for more proactive identification of potential breaches of Force policies and undesirable behaviour
- Comprehensive access controls and system audit reporting ensure that viewing of any or all information is restricted to designated, authorised users and that full accountability is maintained
Protective monitoring that allows you to see, analyse and respond effectively
- Multiple Endpoints
- Across Fixed and Mobile device estates
- Holistic, user-centric audit capture
- Combine data from other systems for greater context
- Apply Policies
- Fully Configurable
- Proportionate
- Manage Centrally
- Act in Real-time
- Uplift monitoring levels on the fly
- Fully Customised Reporting
- More Proactive Governance

Powerful and proportionate Lawful Business Monitoring tailored to your Force’s specific requirements
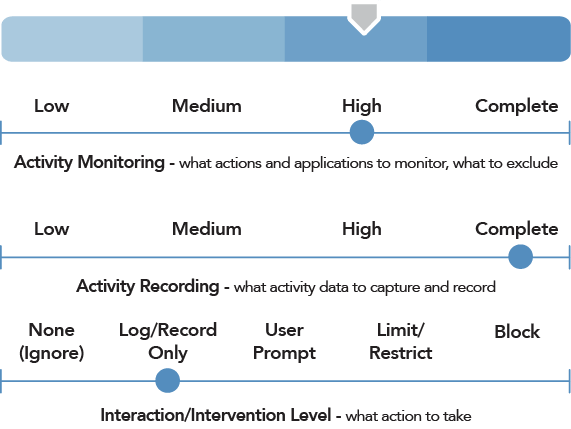
VigilancePro enables each Force to implement the nature and extent of activity capture that is appropriate for their organisation; taking into consideration the need for Lawful Business Monitoring measures to be effective whilst remaining proportionate in relation to staff privacy.
Monitoring and audit policies can be easily amended through configuration to ensure that the solution continues to meet the organisation’s needs as requirements evolve.
Deployment methods to suit your requirements

Virtual Private Cloud
Fully managed, and infinitely scaleable without the need to invest in physical hardware.

Accredited Data Centre
Fully managed in a highly accredited data centre for government bodies and companies not yet ready to embrace the cloud.

On-Premise
Running in your own data centre. Partial or fully managed support plans are available.
Explore More
Put advanced user activity
monitoring into action
We’ve worked with a wide range of different companies and organisations in meeting their insider threat prevention and compliance needs.
Read more on our solutions page, or get in touch to book a discovery session.



