Enhance your Security with Advanced User Activity Monitoring Software VigilancePro®
An insider threat product that allows you to see, shape and stop actions across your organisation.
Advanced User Activity Monitoring Software in Action
Vigilant offers VigilancePro, an advanced user activity monitoring software solution.
Highly flexible and customisable, VigilancePro enables organisations to see and understand the context of their employees’ actions, apply automated policies that shape activity to mitigate risk and access comprehensive audit trails for compliance.
- Multiple Endpoints
- Endpoint Agents
- Apply Policies
- Machine Learning / AI
- Manage Centrally
- Act in Real-time
- Customised Reporting

![]()
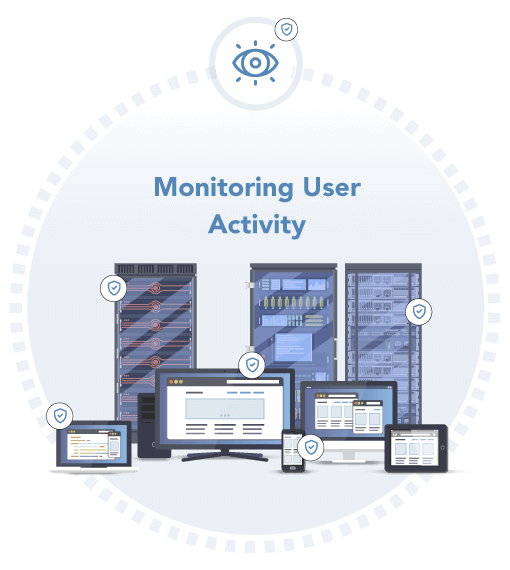
01. See and Understand User Behaviour in Context
VigilancePro is focused on providing a centralised view of all types of activity across your organisation together with detailed context around that behaviour, so that you can ensure appropriate action can be taken.
VigilancePro allows you to:
- Monitor and understand user activity and behaviour on your fixed and mobile device estate across the entire organisation
- Gain deep contextual understanding of user activities to shape or stop unintentional, malicious or fraudulent activities
Endpoint Agent
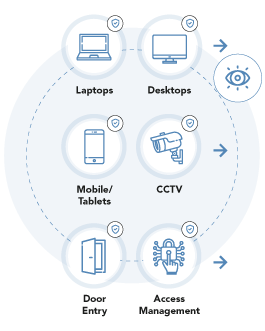
The VigilancePro End-Point Agent identifies and monitors events happening on a system or device and the user activity being performed on them:
- Events on specified systems and applications
- Devices: Desktops, Laptops, Mobile Devices, USB sticks, Door & Digital Access, CCTV, IoT, RFID, PoS
- User Activity
- Instant Messaging, Calls, Audio
- Keyboard input, screenshots, File/Folder access, Keywords and phrases
- Location and Time
The Endpoint Agent has a small footprint, designed with minimal resource and network utilisation in mind. Normal device operation is not noticeably affected, regardless of the level of activity being captured.
If a device goes offline, recording and analysis is persistent allowing for retrospective visibility and analysis.
Mobile Devices and Communications
VigilancePro also enables peer-to-peer encrypted Instant Messager monitoring and auditing including:

- Message – time of event/sender/receiver
- Content in text and images
- File attachments
- Location and geofencing
- Group chats – monitoring joiners and leavers
- Monitoring voice and video calls
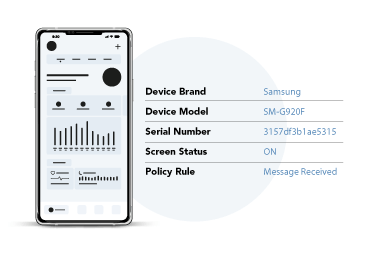
Device Details
Event Details
Location of Device

VigilancePro in Action
A member of a pharmaceutical company’s sales team receives a WhatsApp message on their corporate smartphone from a contact of theirs outside of the organisation that references the code name for a new drug that is currently undergoing late-stage clinical trials. The sales person responds to the message, attaching an image taken on the phone’s camera of an internal memo regarding likely release dates for the drug. VigilancePro immediately sees the code name in the WhatsApp message which triggers an increase in the audit data capture for the salesperson, including the recording of camera images taken on the device and those attached to any outbound or inbound communications. VigilancePro automatically blocks the attachment of the image to the message, preventing the egress of the commercially sensitive data, whilst capturing a copy of the image that the salesperson had attempted to send and raising an alert that the information security team are able to respond to.
![]()
02. Shape Policies Covering Wide-Ranging Data Sources
Our user activity monitoring software is highly customisable so that you can shape policies and actions to meet different business processes and apply them to the entire organisation or at a group, department or individual level.
VigilancePro allows you to:
- Shape policies for security and insider threats or for user training, sensitive data handling and productivity
- Use open and wide data collection from a host of devices and applications to customise responses to specific user actions
- Take a user-centric approach with automated profiling of different users and scenarios based on policies at any level required – from organisation down to the individual
- Gain full context of events across the organisation through the single pane of glass management console
Open Integration with a Wide Range of Data and Physical Assets
VigilancePro is highly customisable, with a set of tried and tested re-usable modules which bring different systems together to build the data pipeline used for applying policies in real-time or providing an audit trail.
A wide range of physical devices and assets, data repositories and machine learning can be connected for bespoke applications, including:

- Devices
- Applications
- Physical control systems
- IoT (Patented Technology for linking physical and digital assets)
- Database and Data Warehouse platforms
- Machine Learning
Cloud Authentication
Single Sign-on via SaaS, integrates existing authentication services (ADFS, WS-Fed or OAuth2)

VigilancePro in Action
A senior manager of a financial services company tries to email classified files to a non-work email address, but is prevented by VigilancePro from doing so. VigilancePro automatically puts the manager on high-level monitoring, applying this heightened level to the manager’s laptop, phone and any corporate device they log on to. No further incidents occur and further analysis reveals it was a genuine mistake.
![]()
03. Stop Actions in Real-Time, Report and Audit
Activities are logged and policies applied to generate a range of responses – from automatically stopping undesirable user actions in real-time to recording user input for auditing and regulatory compliance
Real-time intervention
The VigilancePro Policy Engine applies policies and business rules at scale. User activities and system/device events are detected in real-time and the module automatically profiles the event context and applies the relevant policy.
A range of actions can be taken depending on the policy, including – preventing attempted actions, triggering automatic recording, capturing screenshots or generating real-time alerts via email or SMS.
Full Audit Trail
VigilancePro can be used to proactively capture all actions and events providing a full audit trail for analysis, but take no immediate action allowing for review at a later point. VigilancePro ingests, correlates and analyses data from disparate data sources, highlighting unusual or suspicious activity for further investigation. This enables organisations to bridge data silos ensuring organisation-wide compliance.
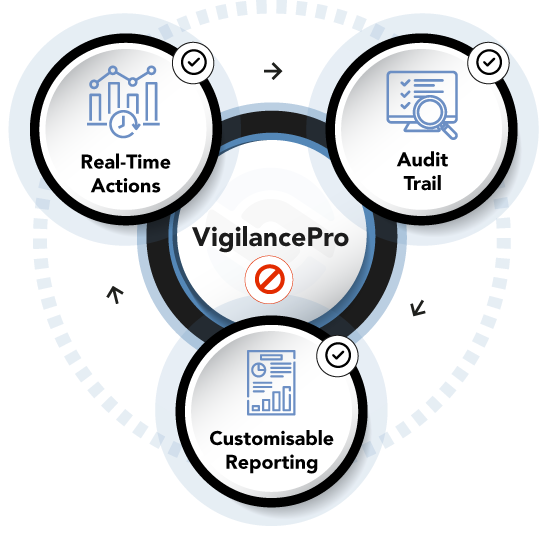
Actionable Customised Reporting
Reporting is delivered through a secure web-based portal, with pre-defined and ad-hoc reporting options to give instant insight into activities.
VigilancePro is database agnostic so that data can be stored in your preferred data warehouse and queried using Microsoft SQL Server, PostgreSQL, Oracle, modern NoSQL, Google BigQuery and Microsoft Azure SQL.
Policy engine and reporting can be enhanced using Machine Learning to detect new emerging threats and automate complex decisions, using:
- Robotic Process Automation (RPA)
- AI Vision
- Natural Language Processing
- Multi-class Classification
- and more…

The National Intelligent Integrated Audit Solution (NIIAS) (Powered by VigilancePro) is a vital part of the tooling required to support the sharing of the electronic patient record – NIIAS helps with the detection of unauthorised access to data and is the cornerstone of the Information Governance Framework in Wales.
Mr. Darren Lloyd – Associate Director for Information Governance and Patient Safety, Digital Health & Care Wales
Highly Available User Activity Monitoring Software and Support
The Vigilant Applications solution can be deployed on-premise or hosted in an accredited data centre or cloud.
Our managed solutions use Landscape©, our automated Desired State Configuration (DSC) bot to make sure the system remains healthy and reliable and available, with automatic failover and No single Point of Failure (NSPOF).

Virtual Private Cloud
Fully managed, and infinitely scaleable without the need to invest in physical hardware.

Accredited Data Centre
Fully managed in a highly accredited data centre for government bodies and companies not yet ready to embrace the cloud.

On-Premise
Running in your own data centre. Partial or fully managed support plans are available.
FAQs
What is user activity monitoring software and why do I need it?
In today’s technological world, employees of almost every organisation use computing systems in one form or another. While these systems enhance operational efficiency, by necessity they also provide direct access to data – often of a highly sensitive nature – to those employees, in turn exposing the organisation to the potential risk of accidental or even deliberate misuse of that data.
User activity monitoring software provides the capability to detect, measure and contain undesirable behaviour of trusted user accounts (those who have been given legitimate access). It does this by monitoring user activity across the enterprise and identifying where individual events, or patterns of events, may pose a risk to the confidentiality, availability, or integrity of the organisation’s data.
With data now at the heart of every enterprise’s operation, and almost certainly one of their most valuable assets, protecting it from risk of misuse by employees is just as important as protecting it from external attack. User activity monitoring software is rapidly becoming an essential component of an organisation’s security technology stack.
How does VigilancePro help protect against insider threats?
VigilancePro provides sophisticated employee activity monitoring and analysis across an organisation’s entire ICT estate. Working in real-time, VigilancePro identifies user actions that may breach prescribed organisational data handling policies, or otherwise pose a risk of a data breach or misuse and, where necessary, automatically intervenes to restrict or block the action.
Comprehensive reporting functionality provides a full audit of users’ actions, together with a detailed analysis of activities across the organisation enabling any necessary remedial measures – be they training or disciplinary steps – to be quickly identified and implemented.
VigilancePro’s unique capabilities support both proactive and reactive insider threat management to bolster security across the enterprise.
Does VigilancePro provide insider threat protection for remote-worker and field-based staff?
Yes. VigilancePro software is compatible with both fixed-infrastructure (desktop PCs, servers etc), mobile (laptops, tablets) and smartphone devices. Activity is monitored across all devices to which VigilancePro is deployed, with actions being recorded against the individual user in question regardless of where, or on what system, it was performed.
Even if the device is not connected to the corporate network or, in the case of smartphone devices, is out-of-signal coverage, VigilancePro continues to monitor users, capture their activity and respond in real-time to shape or block actions that may otherwise present a risk to the organisation.
How will VigilancePro align with my organisation’s specific requirements?
VigilancePro is designed to enable specific insider threat management functionality to be implemented for each customer. Activity monitoring, recording and response policies are configured according to the customer’s individual requirements, allowing the organisation in question to determine what level of oversight is most appropriate for them and ensuring that employee privacy considerations can also be taken into account.
With VigilancePro, both uplifting of user monitoring levels (for example when the user is working with data that is particularly sensitive) and temporary halting of activity auditing (such as when someone accesses an occupational health application) can be automatically applied to enable the organisation to balance security risk mitigation with employee privacy expectations.
How is VigilancePro user activity monitoring software hosted and will my data be secure?
VigilancePro can be deployed using a range of hosting options. Increasingly, customers are electing to use our security-accredited cloud-based Software-as-a-Service offering, which provides a highly cost-effective and, typically, more rapidly implemented solution.
Vigilant Applications holds the globally recognised ISO 27001 certification for information security management, along with Cyber Essentials and Cyber Essentials Plus accreditations.
Our VigilancePro SaaS solutions are hosted in fully accredited, secure cloud environments with appropriate restriction of datacentre locations and data transfer to ensure data sovereignty requirements are respected. Individual customer data is separately processed and stored.
VigilancePro is developed to NCSC Cloud Security Principles and OWASP Top 10 Standards and attested against CREST/CHECK IT Health Check compliance requirements.
Explore More
Put advanced user activity
monitoring into action
We’ve worked with a wide range of different companies and organisations in meeting their insider threat prevention and compliance needs.
Read more on our solutions page, or get in touch to book a discovery session.



