60M
electronic patient record interactions secured daily
100K
police staff secured for professional standards compliance
1M
retail transactions
analysed each day
3M
in real cash recouped
for local government
Insider Threat Management Solutions Delivering Valuable Insight
Are you getting a complete and measured picture of what is happening across your organisation to meet compliance requirements?
With data dispersed across your organisation are you sure that your high-value assets and sensitive data are adequately protected?
For large, widely distributed organisations and inter-agency partnerships, keeping track of user actions across many different devices, systems, applications and data silos can be a real challenge. Malicious and unintentional actions can result in major security issues and missed performance opportunities.
Vigilant delivers effective insider threat management, analysing data across the breadth of the organisation from fixed and mobile devices all the way through to the server, to provide a consolidated view of user activity and identify insider threat vectors.

Protecting Sensitive Data, High Value Assets and Reputation
Vigilant Applications’ user activity monitoring solution VigilancePro® collects, consolidates and analyses data from a diverse range of sources across your organisation – monitoring user actions to help detect and prevent undesirable activities and drive favourable user behaviour for streamlined business processes and improved productivity.
Information on activities and their context is gathered in real-time, taking into account appropriate privacy considerations, from across the organisation so that swift steps can be taken to restrict or prevent undesirable actions and for later analysis, audit and management.
Vigilant offers a highly customisable user activity monitoring solution that can be adapted and tuned for a wide range of insider threat management and compliance requirements.
Learn more about VigilancePROEmpowering our Customers to Secure their Data
“The National Intelligent Integrated Audit Solution (NIIAS) (Powered by VigilancePro) is a vital part of the tooling required to support the sharing of the electronic patient record – NIIAS helps with the detection of unauthorised access to data and is the cornerstone of the Information Governance Framework in Wales.”
Mr. Darren Lloyd – Associate Director for Information Governance and Patient Safety, Digital Health & Care Wales
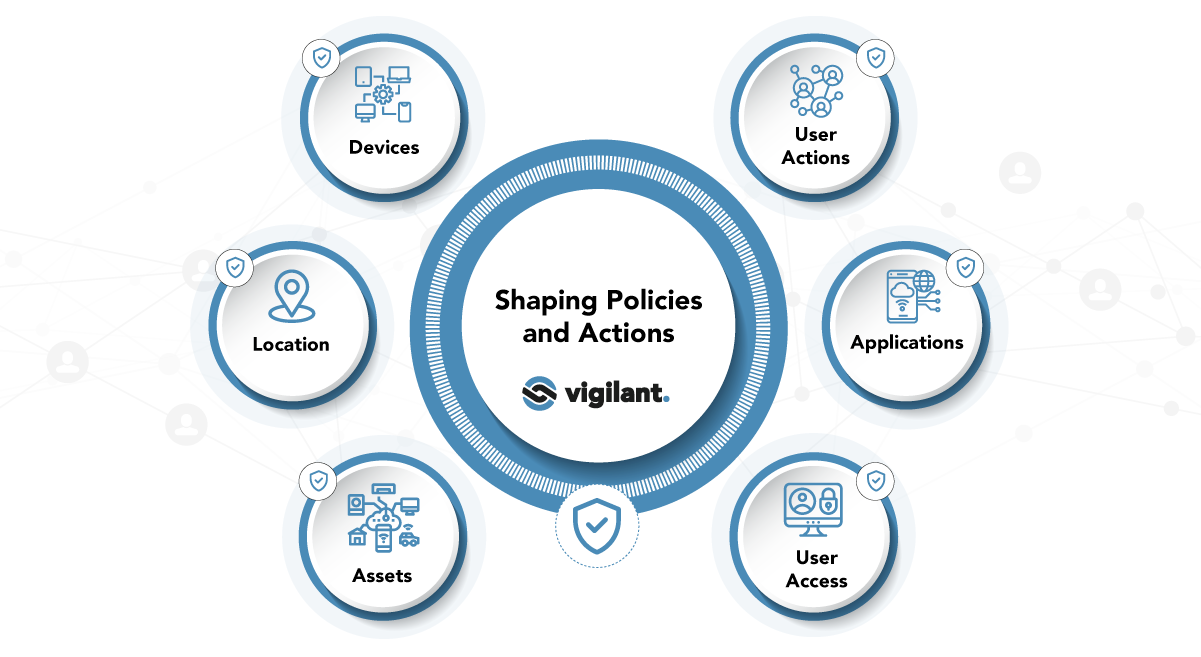
Apply Tailored Policies to Protect the Organisation, Enable Best Practice and Block Negative Actions

Protect the Organisation:
- Sensitive Data
- Intellectual Property
- Regulated Information
- Sensitive Business Information
- Stock and other Assets
- Financial transactions

Enable
Best Practice:
- Prompting against inadvertent misuse
- Reinforcing security awareness
- Implementing security policies
- Ensuring regulatory compliance
- Improving processes

Block Negative
Actions:
- Real-time prevention of specific actions
- Stopping fraudulent activities
- Identification of bad actors
- Protecting company reputation
- Prevent inadvertent misuse
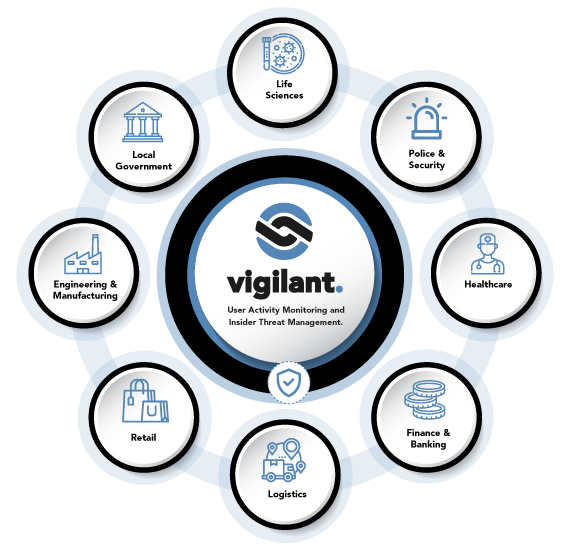
Effective Insider Threat Management across Industry Sectors
We partner with companies and organisations across different sectors to improve data security, mitigate risk and meet compliance requirements through proactive user activity monitoring. Our insider threat solution is highly adaptable and flexible to suit different scenarios:
- Police & Security – Enforcing professional standards
- Healthcare – Protecting access to patient records
- Retail – Safeguarding profits by pinpointing anomalous transactions at point of sale
- Financial Services – Deploying user behaviour analytics to monitor transactions on the trading floor
- Banking – Tracking the use of PII data
- Engineering and Manufacturing – Protecting intellectual property, plans and source code
- Local Government – Paving the way for local authorities to improve services and reduce costs
Intelligent User Behaviour Monitoring
for your Organisation
Get in touch with us to find out more about how Vigilant can help protect
your business assets and reputation.

Automated Data Governance
Protecting Assets and Reputation

Centralised, Context-rich Information
Driving Actionable Intelligence Across the Whole Organisation

Proportionate Activity Monitoring
Balancing Organisational Risk Mitigation with Privacy Protection Obligations
Put advanced user activity
monitoring into action
We’ve worked with a wide range of different companies and organisations in meeting their insider threat prevention and compliance needs.
Read more on our solutions page, or get in touch to book a discovery session.